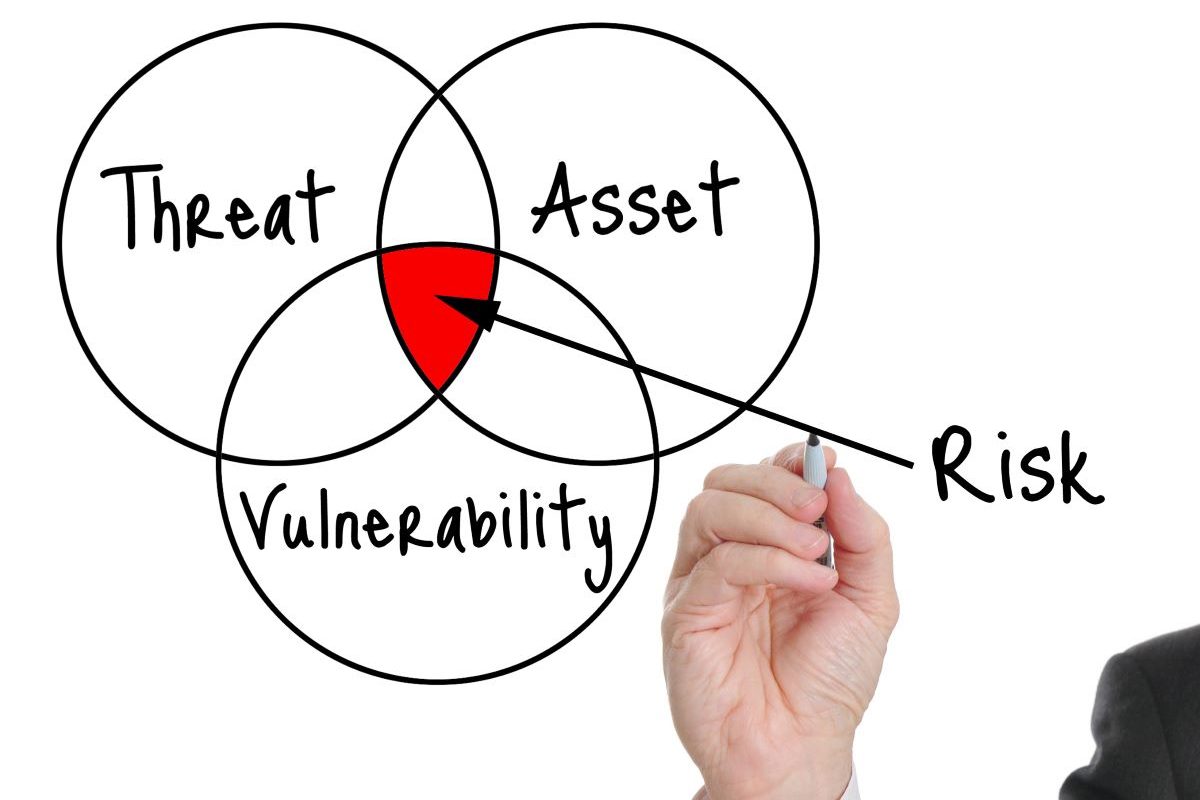
When we talk with business owners, we find that many are flying blind when it comes to cybersecurity. They know it’s important. They know there are threats. To take a comprehensive assessment of your IT security and protocols, you should ask yourself five questions:
- What are my assets?
- What are the threats to those assets?
- How vulnerable to those threats am I?
- What is the cost if a threat becomes a reality?
- What is the solution to avoid a threat?
What are my assets?
It stands to reason that if you want to do a cybersecurity risk assessment, you first need to determine what assets could be at risk. Consider all of the aspects of your business that involve IT, connectivity, and data.
- Here’s a quick list of the assets most businesses have:
- Servers
- Website
- Phone systems
- Documents
- Customer data
But each business is unique and you may have other assets that are unique to your business. Take a few minutes to write down all of the assets that your business has and needs to protect.
What are the Threats to Those Assets?
Now that you’ve identified your assets as part of a cybersecurity risk assessment, what are the threats to each of those assets?
Your business could face significant downtime and disruptions due to:
- Ransomware attacks
- Fire
- Power outages
- Natural disasters like flooding
- Hardware failures
- User errors
- Lack of security on employee’s personal devices
Any of these threats could result in a loss of critical data or costly downtime for your employees. Take the time to identify the threats to your assets and recognize that many assets might be facing more than one threat. For instance, you could lose critical data due to both external threats like ransomware or internal threats like user error.
How Vulnerable is My Business to Those threats?
Now it’s time to assess how vulnerable you are to some of the risks mentioned above.
For instance, if you are located on the 5th floor of a building, flooding from a natural disaster is probably not a risk. However, a fire and the resulting sprinkler and smoke damage might be.
Every business is at risk for a ransomware attack; however, some businesses are more vulnerable than others. How would you answer these questions for your business?
- Have your employees been trained within the last three months on how to avoid phishing scams?
- Does your company have safeguards that require employees to use unique, strong passwords?
- Do your employees understand what immediate actions they should take if a ransomware attack happens?
- Does your company have a protocol in place to monitor backups and make sure they are happening?
If you said no to any of these questions, your business is highly vulnerable to a ransomware attack.
Remote work also opens businesses up to additional risks as employees are using their own devices and less secure networks to log in.
Twenty percent of companies said a breach was a result of a remote worker.
These are a few examples of how every business has different levels of vulnerability to different threats. It’s important to assess your levels of vulnerability so you can better protect against them.
What is the Average Cost of a Cyberattack?
What will a ransomware attack cost you? What will three days of employee downtime cost you? What will the loss of critical data cost you?
The numbers are staggering. The average cost of a cyber attack is $149K. Sixty percent of small businesses cannot absorb the cost of a ransomware attack and must close their doors forever. It’s important to assess the cost, and determine how to minimize it before the worst happens.
What is the Solution to Avoid a Threat?
A comprehensive plan to avoid the threats is important. Here are some things you should consider:
Data Backup

Is your critical data backed up? If not, stop what you’re doing right now and go back up your data.
For most of the threats mentioned above, a complete and recent data backup is the solution. Unfortunately, many businesses do not have a system for backups. Without a specific plan, backups don’t happen or if they do, they may be so outdated that they’re useless.
Employee Training
Did you know that 46% of all small businesses have been targets of ransomware attacks? Of all the companies hit with a ransomware attack, 75% paid a ransom!
Phishing is a common and highly effective way of getting sensitive information. Emails containing links to malicious websites are the most common attack method. The email may contain links to what appears to be the correct websites but are actually spoof sites that look similar if not exactly like the real ones.
Take an hour this week and meet with your employees and educate them about ransomware and viruses. Create a company protocol for creating strong and unique passwords. Remind them that they are the first line of defense in protecting your network. It only takes one employee clicking on a dangerous link or using a weak password to put your business at risk.
Hardware Updates and Monitoring
A system failure can result in years of lost data or extended downtime. It’s important that you’re using up-to-date technology and that you’re monitoring hardware for potential problems.
Recently, one of our customers almost lost an email server. We were monitoring their hardware and noticed an issue with a failing hard drive. We immediately notified them about the hard drive on their on-premise Exchange server before it showed any real external symptoms. We ordered a replacement drive and installed it with zero issues or hiccups. Within days of replacing the first hard drive, another drive suddenly died.
If we had not been actively monitoring the hardware on that server, both hard drives could have failed simultaneously, which could have resulted in complete data loss of years worth of email data! Thankfully, we caught it before it became an issue and our customer was able to stay focused on taking care of their customers instead of dealing with lost emails.
Software Updates
Malware and viruses are constantly evolving, and software updates are designed to combat new and changing threats. If your software has not been updated recently, you’re vulnerable to threats that you could have avoided.
We’re Here To Help!
We know this list can seem a little overwhelming for business owners, and it’s important to remember that you can take proven steps to protect yourself. That’s why we’ve been helping businesses protect their IT for nearly 30 years.
Would you like to know specifically where your business might be facing cybersecurity risks? We can help you identify your business’s IT vulnerabilities. In 2022, it’s time for peace of mind that your business’s critical data and network are protected from bad actors. Give SandStorm IT a call at 901-475-0275 to discuss how we can help.
here.