Recently, we have seen a dramatic increase in the amount of phishing cyber-attacks aimed at Office 365 users. It’s so bad that almost three quarters (71.4 percent) of corporate Office 365 users have at least one compromised account each month, according to a report by Skyhigh Networks. If you are not taking Office 365 security seriously, you should.
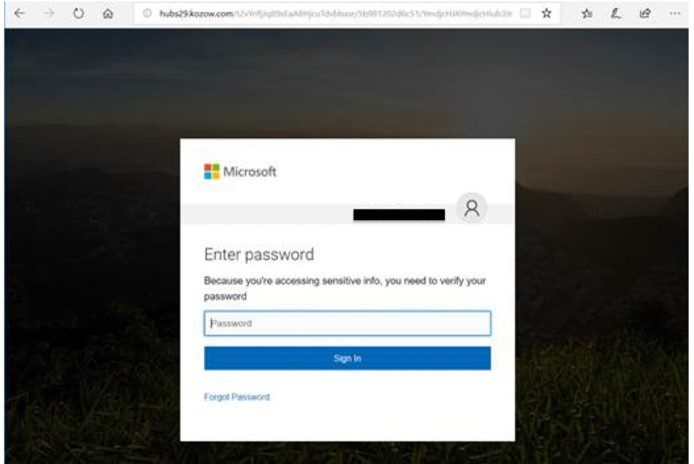
Most recently, attackers are sending out messages to potential victims from a previously compromised Office 365 account’s address book. The objective is to get access to your office 365 account to attempt further attacks or to transition to spear phishing attacks. The incoming message will likely appear to be coming from someone you know. Typically, these messages will say something related to you having a secure document waiting or some other action is required that requires you to login to your office 365 account. These messages will have a link in them that will take you to a fake Office 365 portal page requesting you to sign in. This link isn’t real, and is actually designed to steal your Office 365 credentials, giving them full access to your account. These pages are virtually indistinguishable from the real deal aside from the Web Address at the top of the page. Here’s an example:
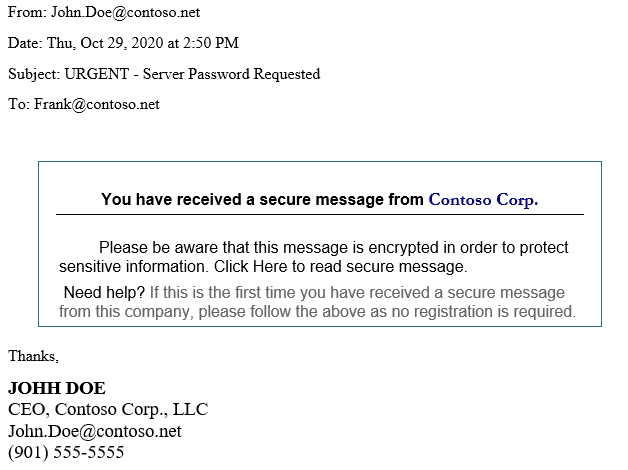
The following is an example of what we’re seeing in these phishing attempts. In this example the attacker gained access to the CEO’s email, and has copied it down to the signature. The attacker will often establish rules that will delete email replies, so the victim is none the wiser unless they check their deleted items regularly.
We recommend that you reach out us in order to put together a plan to establish Multi Factor Authentication and to review your Office 365 security settings. Multi Factor Authentication will help prevent unauthorized logins to an account of members for your organization, even if they fall victim and give up their credentials. Two Factor Authentication (2FA) is a form of Multi Factor Authentication. Typically, 2FA requires a password and a code on your mobile device to be able to sign in.
If you receive one of these messages, we also recommend you reach out to the correspondent via telephone and check in with them. They may be unware that they have been compromised.
