Latest Posts from Our Blog
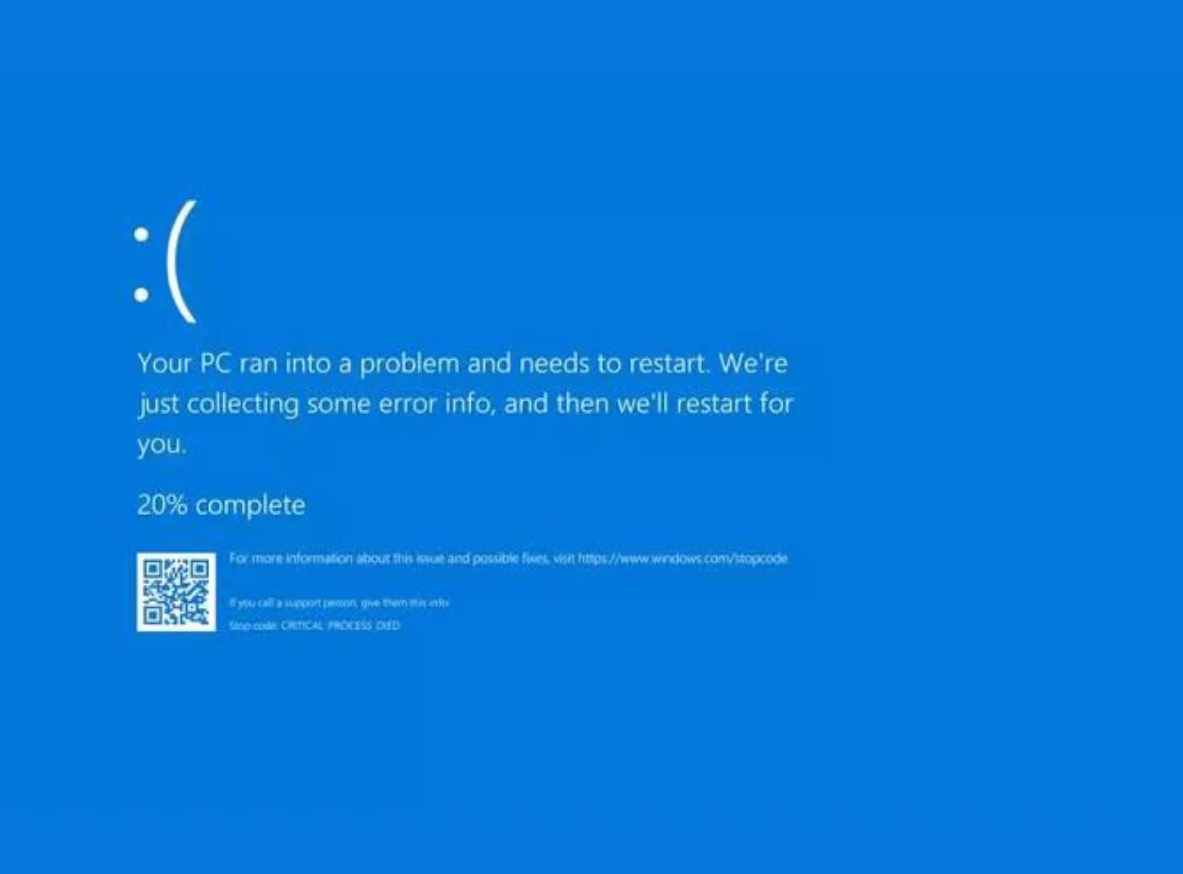
In today’s digital landscape, operational disruptions can arise from unexpected sources, highlighting […]
In the ever-evolving landscape of cybersecurity, recent breaches have underscored the need […]
In today’s digital age, cybersecurity is a critical concern for businesses of […]
In today’s digital age, cybersecurity is paramount. With the increasing number of […]
In today’s fast-paced business environment, efficient data management is crucial. Network Attached […]