A new vulnerability was found that takes advantage of a flaw in the print spooler application within Windows. According to Microsoft “A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations. An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.” (Source: Microsoft MSRC). This means that an attacker could take full control of your system.
What does this vulnerability do?
Windows has a native feature called a “Print Spooler” that is enabled by default. Its job is to manage print jobs being sent to the printer or print server. The issue is that an attacker can use the Print Spooler to perform file operations, including running code with System permissions. This would permit them to do whatever they wish: view data, delete data, create accounts, install programs, etc.
What versions are affected?
All versions of Microsoft Windows operating systems are vulnerable, including the current versions: Windows 10, Windows Server 2012, Windows Server 2016, and Windows Server 2019.
What should I do?
Users are being urged to update Windows as soon as possible. You can do to Start > Settings > Updates & Security > Check for Updates.
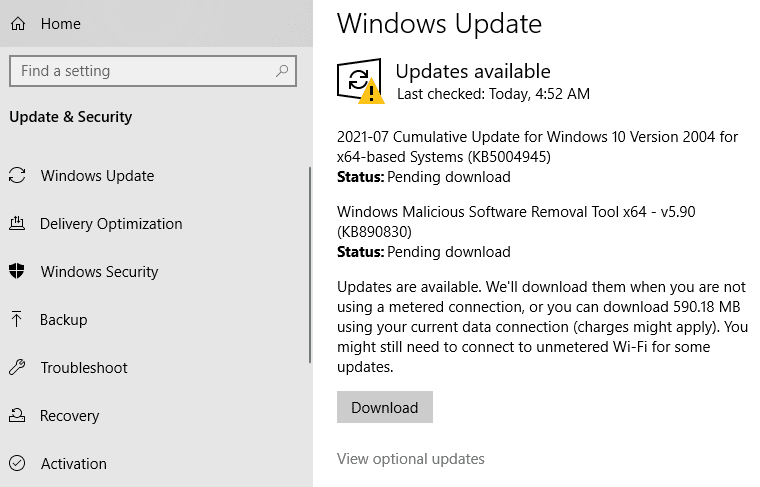
You should see an update “KB5004945” available for download. It’s worth mentioning that you should plan for the required reboot once the installation is complete.
If you have any questions about this update or any other patch questions, feel free to reach out to the cybersecurity experts, SandStorm IT. For cybersecurity updates, feel free to subscribe to our newsletter. You can give us a call at 901-475-0275.
